This might be done when trusted external hosts exist that are not located on networks directly connected to the firewall. To see what you need takes a bit of attention. While testing you could have Snort log to the system logs so you can keep an eye on it: Blocked hosts can be automatically cleared by Snort at one of several pre-defined intervals. The update start time may be customized if desired. It's important to remember that Snort will require more system resources each time an additional category is turned on.
| Uploader: | Akigal |
| Date Added: | 22 September 2012 |
| File Size: | 23.72 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 95879 |
| Price: | Free* [*Free Regsitration Required] |
Installing Snort for IDS/IPS on PfSense | Vorkbaard uit de toekomst
These are some of the most popular Snort rule categories that you may want to enable. This website uses cookies As a user in the EEA, your approval is needed on a few things. This is used to detect comment spam.
Snort is an intrusion detection and prevention system. At the top of the rule list is a legend showing the icons used to indicate eules current state of a rule. Generally this page is only used to disable particular rules that may be generating too many false positives in a particular network environment.
Easiest for the purpose of this document is to create a free Snort account and use Snort with the 30 days old list, get to know the system and then either change to Suricata or pfsensee for Snort.
The Date column shows the date and time the alert was generated. Be sure they are in fact truly false positives before taking the step of disabling a Snort rule! If there is a newer set of packaged rules on the vendor web site, it will be downloaded and installed. Targets known botnet command and control hosts.
These may be created and managed on the Pass Lists tab. The recommended update interval is once every 12 hours, but you can change this to suit your environment.
IDS / IPS — Snort Rules | pfSense Documentation
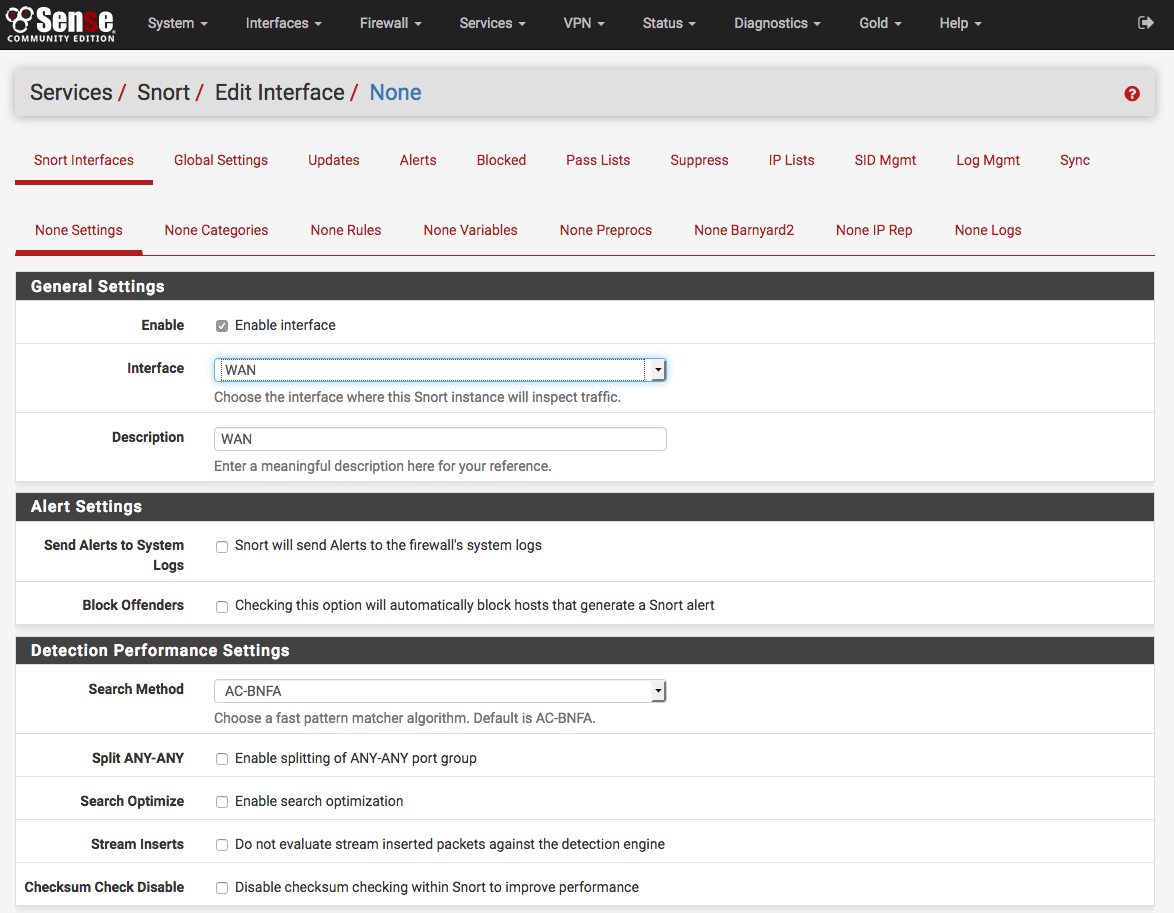
If either of the Source or Destination addresses are currently being blocked by Snort, then a icon will also be shown. Click the Snort Interfaces tab to display the configured Snort interfaces. Please choose which areas of our service you consent to our doing so. Once it has started, the icon will change to as shown below.
Sign in or sign up and post using a HubPages Network account. The Snort settings page will appear in the services menu of the web interface. Preprocessor and Flow Settings There are a few settings on the preprocessors settings page that should be enabled. If it's not visible, make sure the package is installed and re-install the package if needed.
Set Up Intrusion Detection Using Snort on pfSense 2.0
Select both checkboxes to enable detectors and rules download. Locate Snort from the list of packages and then click the plus symbol on the right side to begin the installation. Note that a Pass List may not be deleted if it is currently assigned to one or more Snort interfaces.
The following screenshots are examples of identified services and applications: HubPages and Hubbers authors znort earn revenue on this page based on affiliate relationships and advertisements with partners including Amazon, Google, and others.
False positives can frequently occur with the more secure policies, and careful tuning by an experienced administrator may be required.
Go back to the Snort Interfaces tab and click the Restart icon for the interface you edited. If you want the most up-to-date protection, you should obtain a subscription.
We partner with Say Media to deliver ad campaigns on our sites. To run the manual update, click on the updates tab and then click pfssnse update rules button.
The subscriber release set is the most up-to-date set of rules available. It's not uncommon for a PC on the LAN network to become infected with malware and begin launching attacks on systems inside and outside the network.
It can be configured to simply log detected snorrt events to both log and block them. This is highly recommended for commercial applications.

Comments
Post a Comment